Zero Trust Access
Securely connect to all your devices











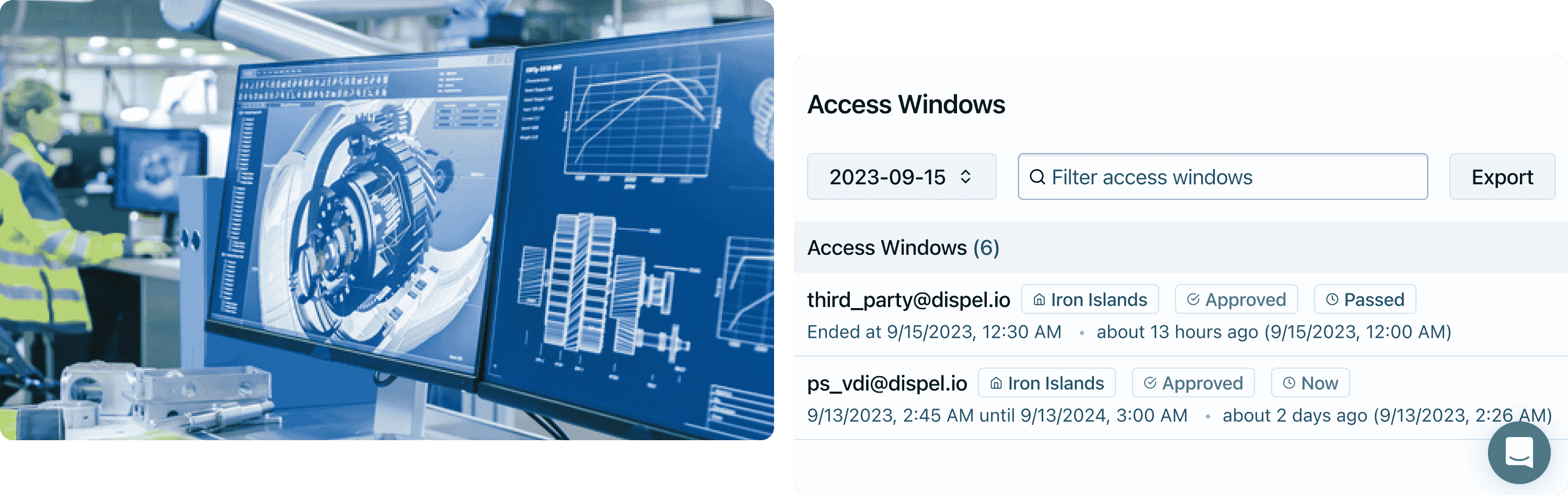
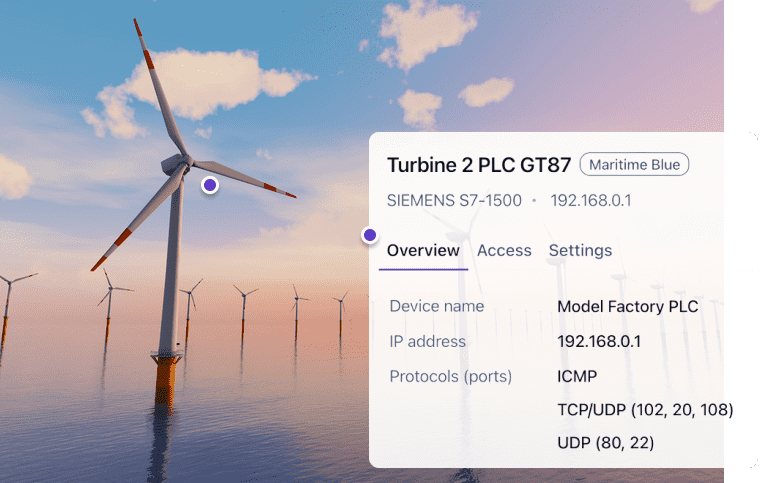












Intelligent, automated installation and debugging tools give you complete control over your Dispel deployment.
All backed by our award-winning global support team and industry-leading SLAs.