If you feel like there is a regulatory framework for just about everything these days, you are not alone.
Today’s framework is the Chemical Facility Anti-Terrorism Standards (CFATS) Act of 2014 which applies to any chemical facility in possession of one of 300 Chemicals of Interest (COIs).
This framework is broken into 18-Risk Based Performance Standards (RBPS) developed by the Department of Homeland Security. Of those 18, RBPS-8, directly focuses on cybersecurity.
The language of the directive is as follows:
“Deter cyber sabotage, including by preventing unauthorized on-site or remote access to critical process controls, such as Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCSs), Process Control Systems (PCSs), Industrial Control Systems (ICSs); critical business systems; and other sensitive computerized systems;”
Fortunately, DHS has broken that concept down into more prescriptive rules for different classes of networked systems – Critical Business Systems, Critical Physical Security Systems, and Critical Control Systems.
For all three, the focus is primarily to limit and control physical and remote access to these networked systems. There are six key elements that stick out:
- Access control with least privilege
- Deactive outdated accounts.
- Be smarter about passwords
- Training
- Define allowable remote access
- Implement an Intrusion/Threat Detection Tool
1. Access control with least privilege
Least Privilege simply entails giving a user or user group the absolute minimum access they need to get the job done.
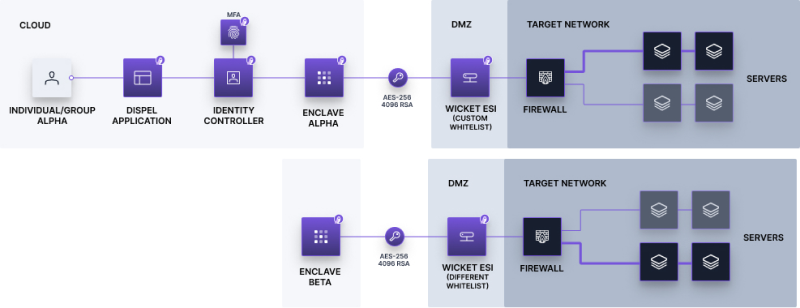
Look at how we implement least privilege at Dispel. Whenever we create an encrypted pathway to a critical network, we create a list of users authorized to connect to the network and then whitelist the resources within the network available to each user.
Different pathways might go to entirely different networks or facilities, and each can have its own whitelist. Each user only has access to what they absolutely need to accomplish their job. They can't access additional resources, and can't even see the pathways to other resources/facilities.
2. Deactivate outdated accounts.
From RBPS-8:
"Ensure that accounts with access to critical/sensitive information or processes are modified, deleted, or de-activated when personnel leave and/or when users no longer require access."
There's a huge rotating cast of characters and our to-do lists are 10,000 things long, this is where most mistakes are made. We've all been there, and until now there was really no way around it except to juggle every Active Directory account in your organization.
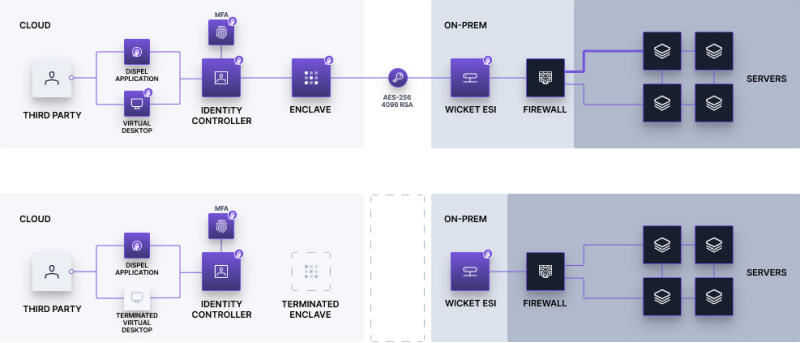
But even with accounts properly disabled, a disabled active directory account is still not secure enough. In that scenario, an unauthorized user still knows where the entry point to the perimeter of your network is. If that user is then phished, an adversary would now know where to start their attack.
A more complete security posture involves not just locking the door, but burning the bridge that got them there.
An unauthorized user should never know where your network perimeter resides. This may sound hard, but with the proper tools, it's completely doable. People shouldn't have access to your systems when they don't need them—why take the risk?
Dispel built a scheduling tool to programmatically destroy the pathways during off hours, or at the end of each project.
3. Be smarter about passwords.
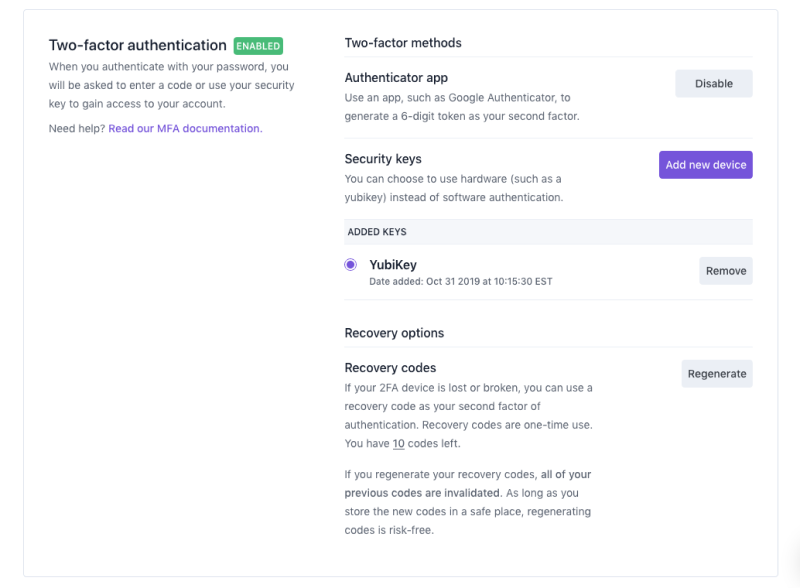
We all get this concept by now – always use at least one uppercase, one lowercase, one number, and one special character in a password with at least 8 characters. But, to take it a step further (and make everyone's lives easier, actually), your teams should implement a good password manager which generates super strong, unique passwords for each service.
Make sure all accounts related to your business are protected by Multi-Factor Authentication, whether that is a good Temporary One-Time Password solution or a hardware device like a Yubikey.
Encourage your employees to use these tools for their own accounts at home. It is better for businesses if their bank information stays safe as well.
4. CFATS Training
We’ve all been told humans are the weakest link, and yet we constantly throw new, more secure tools at them and tell them to re-learn how to do their job.
Implement a tool that invisibly enforces it, so your employees can spend more time doing what you were actually paying them for in the first place.
5. Define allowable remote access.
Getting this right requires a multi-faceted approach. A strong firewall is a great start and quite simply a necessity. However, if you sit a firewall at your perimeter and let the cesspool of the internet at it, a zero-day will find its way in.
Instead, keep that network offline as it should be. Create time-based access pathways only when needed, and ensure that your network detection tools are finding real threats rather than false positives. End-to-end encryption is a must, and if you do not trust the end user’s device, consider forcing them through a clean virtual desktop.
6. Implement an Intrusion/Threat Detection Tool
Some CFATS threat detection tool tips include:
- Make sure the tool you choose is compatible with the protocols on your legacy devices.
- Pick a tool that will assist with asset inventory/management.
- Focus on what the implementation requires, including how aggressive the download and maintenance load is on your legacy devices.
Hopefully, this information has been helpful. If you get these six facets right, your organization will be well on its way to complying with CFATS! If you need support with cybersecurity protocols, connect with our team today.
Your systems should work, and your network should be protected with the strongest security possible. With Dispel, protect your network with Moving Target Defense.
